Medium suspended my account so here is a PDF version of this post that you can download.

In the last few years, many people have realized that Bitcoin is not anonymous, and some of them have realized it with dire, life-destroying consequences.
Bitcoin is pseudonymous and some have learned this lesson on the bitter end of a long prison sentence. The Bitcoin blockchain while remarkable and revolutionary, is at it’s core, an immutable public ledger.
This means that every single transaction is unchangeably recorded and verifiable by every other participant in the network as long as electricity and the internet exist.
This is not an optimal state of affairs for those who require privacy.
I am not going to delve into who needs privacy and why because it is a commonly accepted give in that privacy is a fundamental human right that everyone needs, among civilized peoples.
This guide will show you the reality of using Bitcoin anonymously in 2019.
This post may express views you don’t agree with, I don’t care. Go read another blog if it bothers you.
Our foes are state-level attackers. That means governments, militaries, intelligence agencies, tax collectors, law enforcement, and other jackboot thugs of the world banking cartel.
Our foes will use the tired but common excuses of drug trafficking, money laundering and terror financing as the age-old boogeyman to scare you into submission allowing them to strip you of your privacy and freedom, but we know better.
So how can we tell these rent-seeking parasites to suck it, and flip them a giant middle-finger?
How can we spread financial freedom and privacy in the name of a truly free market?
How can we promote economic liberation from the yoke of a debt-based economy, ensuring a better and more prosperous future for every man, woman, and child worldwide?
I thought you’d never ask.
Step 1. Always use cash to get in and out of BTC
Never, ever use any service that requires AML/KYC. This is how law enforcement ties your real name to your Bitcoin address, exchanges are more than happy to cooperate.
Bisq is the best alternative for buying and selling Bitcoin without AML/KYC. It’s a decentralized peer to peer Bitcoin exchange that lets you buy/sell Bitcoin with a variety of payment methods.
AML/KYC or more precisely known as Anti-Money Laundering/Know Your Customer laws (Assholes Monitoring Life/Killing Your Creativity) are completely idiotic.
It doesn’t prevent any money laundering or terrorist financing and creates an onerous regulatory burden on businesses who have to comply with extortionary so-called “regulatory agencies” in order to operate.
AML/KYC regulations are designed to create an unnecessary paper trail, instead of actually stopping crime from occuring.
It’s nothing but a slightly more polished presentation of common “mob-style” racketeering with suits and ties and licenses.
Contrary to popular belief, Terrorists are funded by governments and money-laundering is a non-crime.
Even if you believe money-laundering is a criminal act, banks are the biggest perpetrators of this crime.
If you buy or sell Bitcoin from an exchange which has all your AML/KYC information you must anonymize your coins.
The disruption and innovation that Bitcoin offers us, is to get rid of these middlemen interfering with the market, the money supply, and the economy overall.
We can now transact directly peer to peer with nobody taking a cut, or trying to interfere.
This is the actual end result of AML/KYC:
No personal freedom and total financial surveillance for everyone, while terrorists and criminals operate with impunity regardless.
In other words, AML/KYC is garbage.
This conclusion does not even consider the higher costs of these financial services for customers who manage to jump through all the hoops of providing an intrusive level of personal information in order to be approved.
This added cost is the blood that the parasites are consuming.
It is a direct consequence of the regulatory compliance costs these businesses face. After all, a tick needs to suck blood from its host.
Step 2. Never reuse Bitcoin addresses
Not even once!
Re-using a Bitcoin address is a massive privacy and security risk.
It makes it easier for blockchain analysis agencies to use heuristics to deanonymize you, as well as others who may have transacted with you.
Reusing addresses is the virtual version of spreading an STD.
The best practice is to use a new Bitcoin address for every single payment you receive, and never send money twice to the same exact Bitcoin address.
Luckily many of the newer wallets are Hierarchical Deterministic, which means that you can generate an unlimited number of public addresses from a single seed, as well as recover the wallet completely, from the very same seed.
Most newer wallets are still SPV wallets, however, and are vulnerable to a wide variety of security vulnerabilities.
The only wallets I can even feel comfortable recommending to others, are the wallets I really use in my day to day.
I use Wasabi on my laptop, Samourai on my phone, Electrum for my BTCPay server, and a Cold Card as my offline cold storage solution. Cold Card and Electrum allow you to sign transactions offline, for added privacy and security. Signing transactions offline also
Step 3. Never use a wallet that uses Bloom Filters (BIP 37)
Bloom filters are defined as:
A filter used primarily by SPV clients to request only matching transactions and
Ok, now that we have established that, why does it matter if you use an SPV wallet that utilizes Bloom Filters? Bloom filters were introduced for security, right? Yes, but the implementation has lots of systemic flaws.
Without getting too technical and boring you to tears, I will refer to the Breaking Bitcoin SPV security PDF. In this document it states that an attacker could possibly:
- spoof full-nodes
- block SPV requests
- spoof SPV requests
- sniff out SPV requests
- block SPV answers.
These vulnerabilities come from the fact that SPV wallets do not verify the entire blockchain in all its immutable glory, they only verify headers, which leaves them open to these avenues of attack.
Electrum, a wallet I recommended above, is a thin-client SPV wallet that uses Bloom Filters, which could be risky to your privacy.
If you use Electrum with your own Bitcoin full
Step 4. Use an anonymity network or VPN like Torguard
Shameless plug: Torguard Anonymous VPN works against the great firewall of China & internet crackdowns in Iran, the link is a special offer from our partners at Torguard, which supports our site, Coincache.net.
Contrary to popular belief Tor is not the only anonymity network. There are others like I2P, Bitmessage, Zeronet, and Freenet that are engineered towards privacy security and anonymity, although at varying degrees of accessibility to the non-technologically inclined.
Always connect to the internet through a
How do the attackers actually attack our privacy?
In this section, I will address some of the techniques an attacker might use to deanonymize you and compromise your security.
I will heavily rely my upon my layman’s understanding from firsthand experience and reading a bunch of blog posts about online anonymity and the presentation by Jonas Nick of Blockstream linked above “Bitcoin Privacy in Theory and Practice” which was given in Zurich in March of 2016.
I want to take a moment to say free Ross Ulbricht!
You can donate to his cause here: https://freeross.org/donate/
Blockchain Forensic Analysis in a nutshell
Blockchain forensic analysis has been marketed as a surefire way to stop crime and people trying to use Bitcoin for evil and nefarious reasons like buying weed from the Mujahadeen off of the dark web.
Blockchain analysis has become a billion dollar industry with blockchain forensic services charging top dollar for their analysis to law enforcement governments, banks, and major Bitcoin exchanges worldwide.
I don’t want to pick on Chainalysis (or Bitfury) but they are hands down, the most famous such firms, although many others exist. Chainalysis will give you a good idea of the services these types of firms offer: activity monitoring reports, cyber-threat intel, and enhanced due-diligence tools.
These kinds of forensic blockchain analysts use a method of guessing what is actually taking place on the blockchain, in the sense of monitoring movement of funds. They do this with a technique called heuristics.
Jonas Nick claims a 70% recall rate with his blockchain analysis, which means that with one single
While this is concerning, we can use tools which attack these heuristic assumptions and make them invalid, allowing us to take back our privacy.
OK, so what are heuristics?
Heuristics are basically imprecise assumptions that are precise enough for the job at hand.
In Bitcoin, this means using software and algorithms to monitor the blockchain and movement of UTXOs to try and deanonymize users.
According to Jonas Nick, there are various heuristics utilized by blockchain forensic analysis companies like
I am not qualified to speak on the specifics but the simplified summary sounds something like this:
Bitcoin Blockchain Analysis Heuristics Types
(from: Bitcoin Privacy in Theory and Practice, presented by Jonas Nick of Blockstream in Zurich 2016)
Multi input Heuristic, assumes all inputs are from the same wallet
Shadow change Heuristic, analyzes change addresses that have never before been on the blockchain, lets blockchain analysis experts know who is the sender and who is receiving funds
Consumer change Heuristic, transaction from consumer wallets have two or
Optimal Change
These different techniques are used by themselves or in varying combinations in an analysis technique called “clustering“.
Clustering allows analysts to follow the movement of funds from wallet to wallet, identify senders and receivers, and deanonymize and identify users themselves by linking addresses to a real-world identity.
Clustering is used on individual wallets (or
Since heuristics are just assumptions about what’s actually happening, they can be attacked by making those assumptions fundamentally unreliable.
Privacy-conscious wallets like Wasabi & Samourai have incorporated such features into the wallets themselves as countermeasures to blockchain analysis.
For example, Samourai has Stonewall, Ricochet, and Paynyms, which make transactions in such a way that many of these heuristic techniques become invalid and uncertain.
Wasabi has so many privacy-protecting features, that I will cover them in its own section.
What can we do to minimize risk?
- Run and use a Bitcoin full-node, so you can broadcast and verify your own transactions.
- Run your Bitcoin full-node as a Tor hidden service.
- Use Wasabi as your desktop wallet and Samourai on your mobile. Learn to use the privacy features.
- Use a Cold Card as your cold storage hardware wallet.
- Never use any exchange or service that has your AML/KYC info. Buy and Sell Bitcoin with cash.
- Don’t tell people you own Bitcoin and never talk about our Bitcoin on social media profiles with your real identity or information.
- Practice good general computer security habits.
- Use Coinjoin or a mixing service to breaking heuristic links to ownership of UTXOs, and maintaining a sufficient anonymity set.
- There are various types of Coinjoin implementations that can’t deanonymize you or steal your funds.
- Zerolink,
Joinmarket ,Tumblebit , and Coinshuffle are all different types of Coinjoins which can’t steal your funds or deanonymize you. - Practice Coin Control like a champ.
Why you should stay away from centralized online mixing services.
There are various Bitcoin mixers or tumblers that are in use by denizens of the dark web. Some are complete scams, others are legit and charge a fee, and still, others selectively scam their customers.
You cannot trust these services
Even if they don’t rip you off, you have no idea how they are actually mixing your coins, if they are providing sufficient anonymity, and you have no guarantees they are not deanonymizing everyone themselves. Using a mixing service is extremely risky.
There are now safer, more secure options called Coinjoins.
What are Coinjoins?
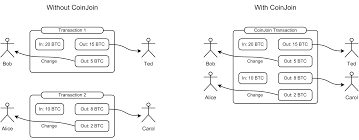
Coinjoins are a method of obscuring ownership of UTXOs by joining the inputs and outputs of many people into a single transaction. If the inputs are all the same size, it makes it impossibe for blockchain analysis to tell whos coins are whos. It was first proposed by Bitcoin core developer Greg Maxwell in 2013.
There have been various styles of Coinjoins which have been developed. They all follow the basic framework laid out by Maxwell, each with their unique approach and techniques.
I will take a look at a couple different implementations and give you a quick overview of each, so you can decide which one is the best for your privacy needs.
Joinmarket
Battle tested, dark web approved.
Joinmarket is a trustless Coinjoin implementation that uses a Maker/Taker model to incentivize users and provide liquidity.
With
As a maker providing liquidity, you can help Bitcoin privacy and fungibility while earning a passive income in fees for doing so. The income in fees is low, but it is also very low risk.
A single
The
An anecdotal testament to Joinmarket’s effectiveness is this guy’s offer to reward 220 Bitcoins to anyone who could help him recover his 440 stolen Bitcoins. He was able to watch the thief send the coins to Joinmarket, and then sadly, the trail was lost forever. Nobody was able to help him or claim any reward.
Tumblebit
It is more than just a
Tumblebit’s payment channels are different than the payment channels employed by the Lightning Network, so it is unclear if the two protocols would be integrated at this time.
Tumblebit’s anonymous payment hub would require users to open a payment channel with the payment hub, similar to how channels must be opened to use the Lightning Network.
Tumblebit’s payment hub would also be second layer scaling solution that could make payments in seconds, similar to the lightning network but it would exist as its own layer 2
Additionally, payment hubs would pool Bitcoin, creating upward price pressure while ensuring anonymity, fungibility, privacy, and scaling.
It is called NTumblebit and was written by Nicolas Dorier, Bitcoin core developer and creator of BTCPay server.
Coinshuffle++
Coinshuffle++ is yet another trustless implementation of
Coinshuffle was first
Coinshuffle is more decentralized than other
Coinshuffle++ is the successor of the original Coinshuffle project. Coinshuffle has had a couple of implementations like
This is for two reasons, the first being that Coinshuffle++ utilizes its own mixing network called DiceMix (DM). DiceMix would need to be integrated with TOR/I2P which would require a lot of development work.
The second is that building a decentralized/distributed network is very challenging. It is hard to fix bugs, everything must be done nearly perfect the first time. It is akin to working on the engines of an airplane while it is still in flight.
Decentralized systems are much more complex to create than a standard implementation.
Coinshuffle is also open source, so feel free to contribute.
Zerolink
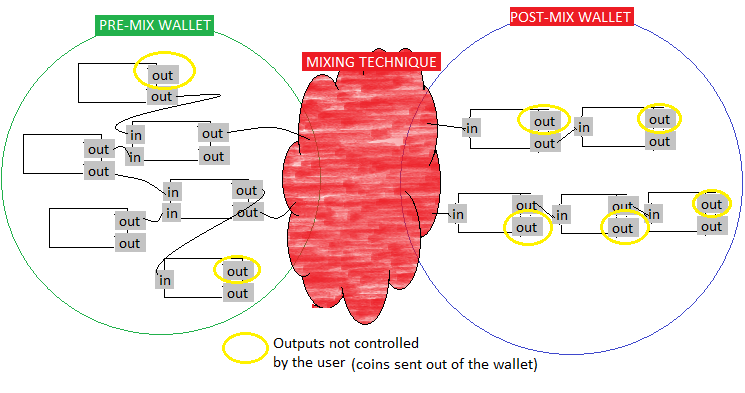
Zerolink has been called the Bitcoin fungibility framework. It is another unique and interesting implementation of
Zerolink utilizes a new technique called Chaumian Coinjoin which is a faster and less expensive method of conducting
Zerolink is billed as being the first
“offer protections against all the different ways a user’s privacy can be breached. The scope of ZeroLink is not limited to a single transaction, it extends to transaction chains and it addresses various network layer deanonymizations”
Nopara73
Zerolink at its core is a 3 part system. It consists of a pre-mix wallet, a post-mix wallet, and a method of mixing coins which
Chaumian
Chaumian
Zerolink provides mathematically provable anonymity to users.
It is also open source and contributions are encouraged.
My experience using Wasabi Wallet
Wasabi wallet is a complete gamechanger for Bitcoin privacy, anonymity and fungibility. It is brand new and has just released version 1.0.5 which you can download here.
Wasabi wallet was created by Adam Ficsor, aka Nopara73. Adam worked on
Wasabi wallet is completely redesigned (from the ground up) version of Adam’s earlier project
Wasabi is the first-ever Zerolink compliant wallet and it’s now live on Bitcoin’s main net.
Wasabi is hands down my favorite Bitcoin wallet. It has forever raised the bar in what a Bitcoin wallet should be, and which features it should incorporate.
Let’s take a look at Wasabi’s features to protect your privacy and anonymity:
- It’s open source, you can audit its code.
- Cross-platform (Linux, Windows, OSX).
- Zerolink Compliant.
- BIP 84 Wallet (only Bech32 Native Segwit Addresses).
- Only light wallet which does not fail against Blockchain Forensic Analysis.
- Built-in high volume mixer/tumbler based on Chaumian Coinjoin.
- Built-in Blockchain analysis tool to help you keep your anonymity intact.
- Built-in advanced coin control feature to help you manage your UTXOs with precision.
- Tumbler cannot deanonymize you or steal your coins.
- Extremely minimal fees of only 0.03%
- Wasabi has made over 2417 BTC fungible since August 1, 2018.
Wasabi is super easy to use and makes coin control simple and easy to understand and use effectively.
It is commonly said that an anonymity set of 50 is sufficient to evade blockchain forensics analysis. With Wasabi this can be achieved in a matter of hours (or minutes if there are lots of other users).
I have been able to achieve much higher anonymity sets than this with my coins. I think the highest anonymity set I have reached is 360, which is extremely high. If I continue tumbling these coins I could keep getting a higher and higher anonymity set.
Coin Control is essential to maintain this level of anonymity, which means using the tools in Wasabi to never mix UTXOs which could deanonymize you. (It’s much easier than it sounds.)
Wasabi utilizes the Zerolink framework of a pre-mix wallet, post-mix wallet
This means after you mix your coins, you can send them to a completely new Wasabi wallet with no heuristic links to your other wallets.
It also allows you to have a wallet for each subsector of your spending, (e.g. Healthcare, Monthly expenses, Discretionary spending, Cold storage, etc.).
This allows you to practice coin control across all your wallets and to control your UTXOs with surgical precision.
You can also send anonymized UTXOs to another wallet or a hardware wallet (send the UTXOs one by one so you don’t deanonymize yourself) for offline cold storage.
All in all, Wasabi has changed the dynamics of Blockchain forensic analysis by making their heuristic assumptions unreliable and gives power back to the Bitcoin user by giving them mathematically provable privacy and anonymity sets.
Samourai Wallet will be the second wallet to be Zerolink compliant and will share many of the same groundbreaking features as Wasabi, but for mobile wallets and spending Bitcoin anonymously on the go.
In Conclusion
Privacy is more important than scaling for mass adoption of Bitcoin. It is also the main reason that the mainstream finance and business words have not fully embraced Bitcoin yet. They need to protect their business’ financial confidentiality from competitors, and Bitcoin’s public ledger is not conducive to this need, yet.
This post is an overview of existing privacy techniques and how you can utilize them yourself.
To actually use these techniques, this blog post should be viewed as a starting point for further research. Make sure you understand all these concepts before attempting to use them in the wild.
Be very careful when using these anonymity techniques, especially if your life depends on it. There are very real consequences to engaging in controversial behavior that may benefit from the techniques reviewed here.
Every single Bitcoin user that cares about personal freedom and financial privacy should be utilizing
The more people who use these techniques the more fungible every Bitcoin becomes, making it more and more like digital cash.
If this article was useful to you or informative and entertaining, you can donate to our site (microdonations via lightning network accepted), or visit our shop and purchase one of the special offers from our site partners.
27 Comments
Jason Trio · January 4, 2019 at 12:13 am
Thank you for the informative post. I’m going to try out wasabi. I buy from a kyc alm exchange. I know it’s not recommended, but it’s easy. I’ll look into bisq as well. Hopefully things get easier for the end user.
mintycosta · January 4, 2019 at 12:37 am
I’m glad you found it useful, thanks for your feedback. Things will get easier eventually. At one point sending email was really complex too until someone figured out a good UX design for it.
satoshi · January 4, 2019 at 3:54 am
this is overly complex… just use monero.
mintycosta · January 4, 2019 at 12:09 pm
Monero is good if you are into alts, but i don’t use alts or care about them
neville carpenter · January 4, 2019 at 7:27 pm
Very useful article already downloaded Samurai on my phone and setting up wasabi now.
mintycosta · January 5, 2019 at 12:48 am
I am happy you found it useful! Samurai just came out with a new privacy feature today called stow away transactions which are like a variety of pay 2 endpoint transactions.
https://twitter.com/SamouraiWallet/status/1081169112741613568
Cb · January 5, 2019 at 12:47 pm
Best way to use the cash Anonymously?
mintycosta · January 6, 2019 at 11:40 pm
wear a hoodie and some shades and don’t tell nobody who you are
jsa · January 5, 2019 at 2:32 pm
Which of the withdrawal options is the most anonymous of those available in Bisq - apart from face2face meetings (which I don’t understand how they work)? Either way, I need a bank account that is not on me to remain fully anonymous? Is there any banking or parabanking service that would make it possible to maintain full anonymity in the storage of funds in national currencies through e.g. the easy to bypass KYC system?
mintycosta · January 6, 2019 at 11:39 pm
You can sell for moneygram, which doesn’t require a bank account
ssss · January 5, 2019 at 2:43 pm
Is there a banking or parabanking system where funds can be held in national currencies and which does not have KYC/AML or is very easy to circumvent? Because I can’t see how I can withdraw funds from Bisq while remaining anonymous. Face2face is rather a weak form of withdrawal and I don’t understand how it works with Bisq and how it differs from localbitcoins.
mintycosta · January 6, 2019 at 11:41 pm
Bitcoin is the parabanking system w/o AML/KYC, but you can get somebody on Bisq to send you cash with money gram and get fiat that way
Charlws · January 5, 2019 at 3:31 pm
Very helpful, thanks for sharing. Great explanation of the mixing tech. Going to give wasabi a try. What do u recommend for people who own bitcoin from Coinbase or other AML/KYC exchanges?
mintycosta · January 5, 2019 at 4:19 pm
Install wasabi and use the coinjoin feature until you get the green symbol with a checkmark, signifying a zerolink mixed coin with sufficient anonymity set. Then practice coin control by not joining already mixed utxos. You can keep coinjoining as much as you like to keep increasing your anonymity set exponentially as well. To move the utxos to another wallet or hardware wallet for cold storage, do it one utxo at a time, it’s tedious but if you you value your privacy it’s the way it must be for now. To spend do it from another wasabi wallet (you can have multiple wallets in the same wasabi app) or move the utxos one at a time to samourai, and spend with ricochet, stonewall and stowaway transactions. The plus with wasabi is you can actively decide which utxos you include in a tranaction. Samourai doesnt have this feature yet…
MrR · January 5, 2019 at 6:19 pm
Thanks for sharing this. This society is going crazy by blocking and banning people that only want to be free. Again thanks and please keep posting these kind of state-of-the-art information.
mintycosta · January 7, 2019 at 12:03 am
thanks for reading, got some more good stuff coming soon.
mintycosta · January 16, 2019 at 3:38 pm
Thanks for reading. I agree we just want privacy and they want full control, something has to give.
cc · January 5, 2019 at 8:24 pm
Thanks for the Article !
mintycosta · January 6, 2019 at 11:42 pm
thanks for reading it!
Paul Amery · January 6, 2019 at 4:23 pm
@mintycosta could you get in touch? I would like to interview you on this topic. Paul
mintycosta · January 6, 2019 at 11:41 pm
email sent
Q · January 12, 2019 at 10:45 am
I buy bitcoins on a P2P network (bitcoin.de).
Is it private enough if I send them to wasabi from there and then on to ledger s?
mintycosta · January 16, 2019 at 3:35 pm
It is private enough if you mix them enough to achieve a sufficient anonymity level (until they are a zerolink mixed coin, green shield with checkmark), and then do not join those utxos together again after mixing them. So after they are mixed, you’d want to send the utxo’s one by one from wasabi to the ledger. Rememeber that you probably want to go overkill on the anonymity set if you’re planning for long term storage. Just to ensure that future analysis techniques can’t deanonymize you like 5-10 years (or more) from now. You could also send them to samourai then the ledger and use some of samourais anonymous sending features like ricochet and stowaway to further confuse the trail.
bitcoin faucet · January 29, 2019 at 11:55 am
Remarkable! Its in fact amazing post, I have got much clear idea about from this article.
mintycosta · January 31, 2019 at 12:38 am
Awesome! I am glad you found it useful!
Luke · January 29, 2019 at 3:40 pm
This is a great guide. Thanks for writing it! I’d be keen to republish it. Mintycosta, could you send me an email and I’ll share the details? Cheers
mintycosta · January 31, 2019 at 12:39 am
Hi Luke, email sent!